airTRFX Automated Penetration Test Summary
Executive Summary
Detectify conducts automated penetration tests and vulnerability scans of airTRFX on a continuous basis. This tool performs tests against web applications, based on the OWASP Top 10 specifications, fingerprinting of content management systems, and the latest trends in vulnerability research. The results of these scans provide EveryMundo with an assessment of the application’s vulnerabilities from the perspective of a malicious actor. By relying on a web-based automated testing provider, such as Detectify, EveryMundo has the ability to monitor and address security concerns 24-7.
Automated Testing Assessment Objectives
- Document and demonstrate likely attack vectors
- Identify specific vulnerabilities that can be remediated to improve security
- Continuously improve EveryMundo’s overall security posture based on the results
Risk Summary
A scan of airTRFX was conducted by Detectify on February 21, 2019. The platform was tested for 700+ vulnerabilities. A Common Vulnerability Scoring System (CVSS) threat score of between 0-2.9 indicates an overall low severity of vulnerabilities – airTRFX was assigned an overall CVSS threat score of 1.8.
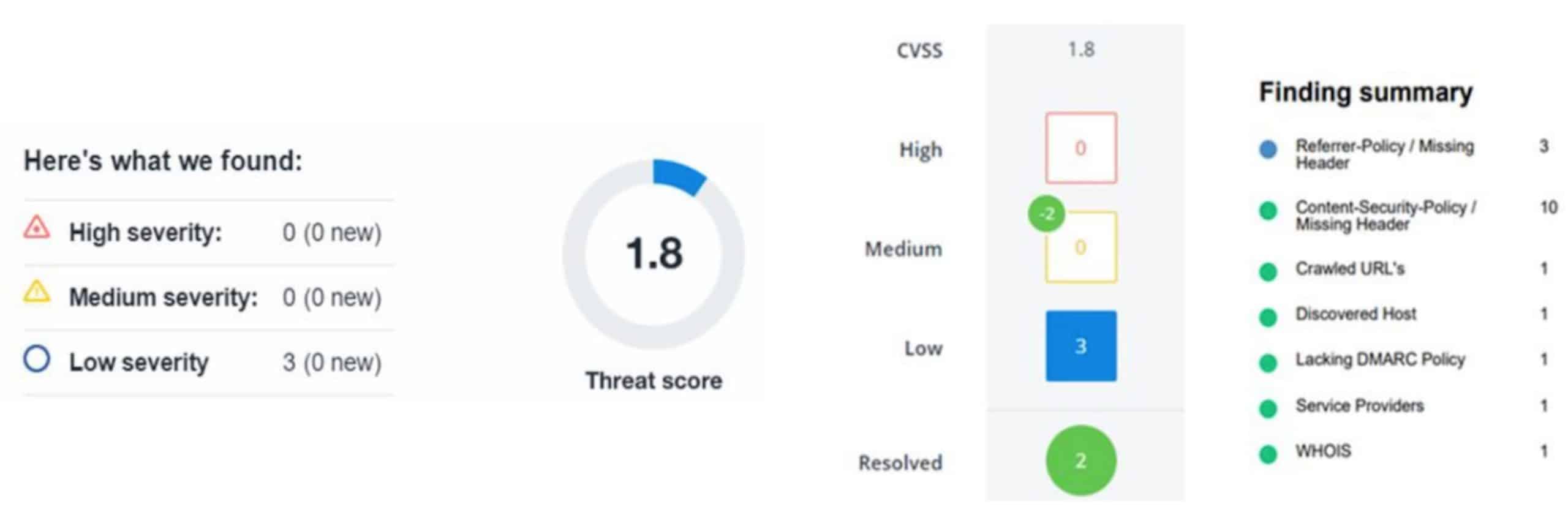
The risk score of 1.8 is driven by a “Referrer-Policy / Missing Header”, which is considered a low severity issue. This type of finding typically indicates that no referrer policy was found in the response and browsers. Browsers may send sensitive information if it is stored in the URL to external websites.
In the case of this airTRFX penetration test, the finding was in a response which does not contain data, because it was a “400 bad request.” For valid requests made against the system which do contain data in the response, the referrer policy header is always present.
Additional Documentation
Additional, detailed documentation regarding the most recent penetration test results can be provided upon request from the customer.
Automated Testing Process Overview
Detectify finds all unique code flows on which vulnerabilities may reside by finding similarities between different URLs as well as repeating content through a system of clustering algorithms. The tools crawls until there’s no more content of relevance instead of stopping at a fixed number of URLs.
Vulnerability Detection
Detectify embraces the OWASP Top 10, an awareness document for web application security and the broad consensus about the most critical security risks to web applications. A variety of key security flaws, including SQL, LDAP, XPATH and NoSQL injections, Cross-Site Scripting flaws, broken session management, remote code and command execution, malware, etc. are assessed.
Detectify’s findings are classified according to the CVSSv2 specifications in order to make it easier for developers to prioritize threats and create risk mitigation plans accordingly.
The Infrastructure and Testing Process
Detectify leverages the Amazon AWS cloud. A scan is completed in six phases, each individually explained in detail below. Full penetration testing and vulnerability scans can be completed by EveryMundo on an on-demand basis. This access allows us to continually monitor and manage our security standing.
1. Information Gathering
Detectify scans the entire airTRFX infrastructure, by, for example, identifying subdomains and hosts.
2. Crawling
After collecting the initial information, Detectify crawls airTRFX to find as many unique URLs as possible within the scope of your domain. While doing this, the tool monitors content to make sure that it’s of no harm to the security of the application.
3. Fingerprinting
This phase is used for extended fingerprinting of the domains The tool attempts to resolve the CMS, the technology stack, the operating system. All this to customize the vulnerability scanning in the next phase.
4. Information Analysis
During this phase, Detectify analyzes the collected data from the previous phases. It looks for incorrectly configured login forms, error messages, database backups and other common flaws and mistakes based on static source code analysis. It also scans for malware using VirusTotal and its many anti-virus solutions.
5. Exploitation
Based on the information gathered in the previous phases, Detectify performs extensive tests using known penetration testing methods as well as the very latest methods in web security.
6. Finalization
During this phase, Detectify finalizes a penetration testing report and removes any “false positives.”
